CVE-TBA: Cleartext base64 format for transmission of credentials within cookies in QNAP TS-x09 Turbo NAS
On the 13th of July 2015 I discovered a clear text base64 transmission of credentials vulnerability within cookies in QNAP TS-x09 Network Attached Storage devices. Full disclosure was undertaken with the vendor and a CVE-ID has been requested from Mitre.
CVE-ID: requested
13th July 2015
Author: Mark Cross
Twitter: @xerubus
WWW: www.mogozobo.com
Summary
A plaintext storage in a cookie vulnerability exists in QNAP TS-109/209/409/409U Turbo NAS devices, including Standard, II, PRO, and PRO-II models running <= Version 3.3.3 Build 1003T. By default, the devices store the username and password credentials within the cookie using base64 encoding. This vulnerability has not been reported for the QNAP TS-x09 devices, however has previously been reported for similar devices by Sense of Security.
Disclosure Timeline
13 July 2015
– Emailed vendor full vulnerability details via PGP email.
– Requested CVE identifier from MITRE via PGP
21 July 2015
– Vendor advised they will not be releasing a new firmware.
– Advised vendor public disclosure date will be Friday 24th July 2015
24 July 2015
– Provided MITRE will full vulnerability details
– Advised MITRE that vendor will not be patching vulnerability
– Re-requested CVE-IDs be released
– Vulnerability published on mogozobo.com
– Vulnerability publicly disclosed via Full Disclosure mailing list.
Status
Published
Tested versions
This vulnerability was tested on the following QNAP devices:
– TS-109 PRO and TS-109 II Version 3.3.0 Build 0924T
– TS-209 and TS-209 PRO II Version 3.3.3 Build 1003T
– TS-409 and TS-409U Version 3.3.2 Build 0918T
Details
The QNAP NAS Management Software, embedded as firmware, is accessible via a web-based interface on all Turbo NAS devices. A vulnerability exists in the method the devices store the username and password credentials using base64 encoding. This attack is amplified by a reflected XSS vulnerability (CVE-ID-requested) and the lack of the HttpOnly flag utilisation.
An attacker may exploit the vulnerability to obtain authentication credentials via sniffing and intercepting network traffic.
Proof-of-concept (PoC)
The following proof-of-concept (PoC) demonstrates the vulnerability:
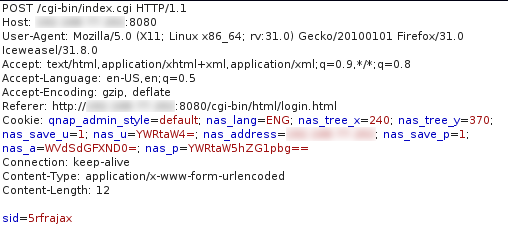
Request:
Cookie value
|
1 2 |
Cookie: qnap_admin_style=default; nas_lang=ENG; nas_tree_x=240; nas_tree_y=370; nas_save_u=1; nas_u=YWRtaW4=; nas_address=<redacted>; nas_save_p=1; nas_a=WVdSdGFXND0=; nas_p=YWRtaW5hZG1pbg== Connection: keep-alive |
The nas_p contents in this cookie contains both the username of ‘admin’ and the password of ‘admin’ in a single string. Should the user tick the “Remember username” checkbox, other variables will be exposed in the cookie. nas_u contains the base64 encoded username, and nas_a contains the username base64 encoded twice.
Decrypted value showing username and password
|
1 2 3 |
$ echo YWRtaW5wYXNzd29yZA== | base64 -d adminpassword |
Amplification by a reflected XSS vulnerability
Example amplification of exploit when combined with my previously reported reflected XSS vulnerability.
Vulnerability solution
QNAP have advised that they will not release a new firmware to address the vulnerabilities.